- IndustryCybersecurity
- Type of projectMobile app development

Meet Keyri - The Ultimate B2B Solution To Secure Your Business And Increase Customer Loyalty.
It deals with three crucial targets of any cyber attack: weak passwords, insecure interfaces, and unencrypted data.

“There was a 424% increase in new small business cyber breaches in 2021. It’s not just about the number - it’s about their systematic nature.”

The story behind…
Steve is a startup owner who had experienced fraudulent activity on customer accounts the other day.
He knows the importance of data security.
Steve turned to IvorySoft with the problem of passwords being publicly exposed, which allows getting access to accounts.
The idea was to eliminate credentials input from the equation at all.

This is how Keyri v.1 was born - a mobile application serving as a trust source to store all sensitive data.
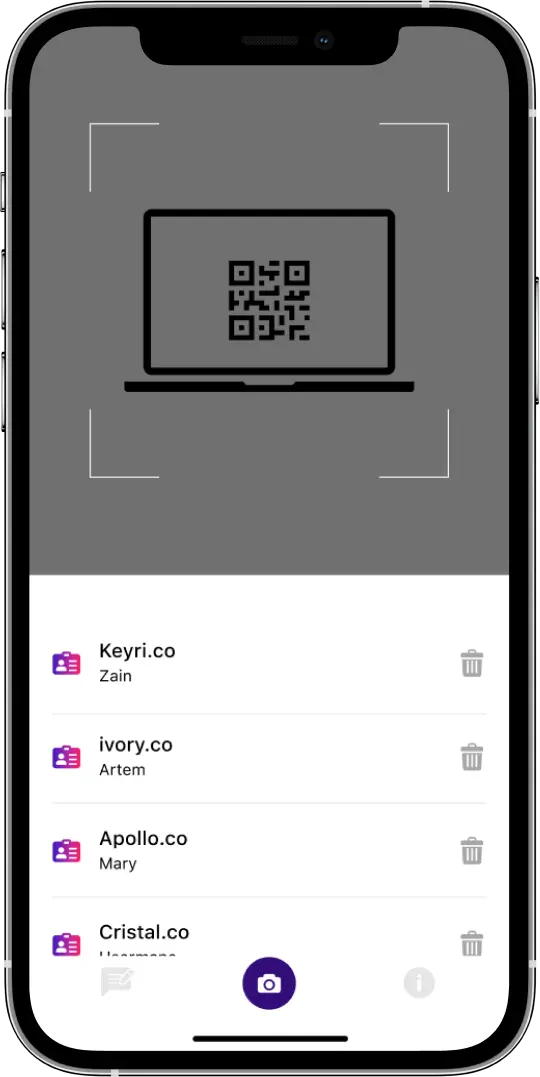

The concept allowed to use a QR code as the way to access any service or platform, which particularly protects from man-in-the-middle attacks.
Each user gets a unique QR code and can enter the system securely. What’s more, even if data is hacked, it cannot be read as it is encrypted.
Steve applied to Y Combinator (an American technology startup accelerator to fund startups) and figured out the approach was not practical.
Businesses want their own built-in authenticator, especially when it’s about dealing with their users or customers.
That way, Keyri developers came up with the idea of white-label SDK.

It is absolutely integrable and tailored to any business package that allows enterprises to get their users or customers signed in or signed up with no risks of a data breach. The team delivers 5 key elements:
- 1Web interface: the place where users log in
- 2Widget providing unique QR codes to users
- 3IvorySoft Backend
- 4Mobile app as a trust source
- 5Company’s backend where authentication is happening
Here’s what businesses get:
- Full control over the service: third parties have no access to any of its part
- The whole concept encapsulated and integrated into the company’s ecosystem
- Free integration, with payment being done for the number of unique users per month
- Significant cost savings as in-house development is an expensive and cumbersome process
- Complete data decryption
- System that identifies cyber threats and provides visibility into the elements related
- QR-code customization to fit the company’s design

BIG
FAT
Brownie Point:
Unique analytics delivering data on:
- Successful and unsuccessful logins, signups, which allows maintaining crystal clear billing and plan pay per leads costs
- iOS and Android users
- Time frames
- Details of each user’s subscription (-s)
- Keyri or white-label users
- In case of man-in-the-middle attacks, unsuccessful logins will tell analysts that the business is being targeted
“Organizations must defend their networks, systems, and users against several major cybersecurity threats.”

Keyri knows how!

